The Psychology of Privacy in Elite Travel
For the ultra-wealthy, privacy isn’t luxury—it’s leverage.
Whether it’s a discreet weekend in the Alps or a business-critical stop in Dubai, high-net-worth individuals (HNWIs) and entrepreneurs are redefining what it means to truly disappear from public view. The rise of digital surveillance, public travel logs, and real-time location leaks has made discretion more than a lifestyle preference—it’s a security measure, a power move, and a personal brand statement.
Why Privacy Now Signals Power
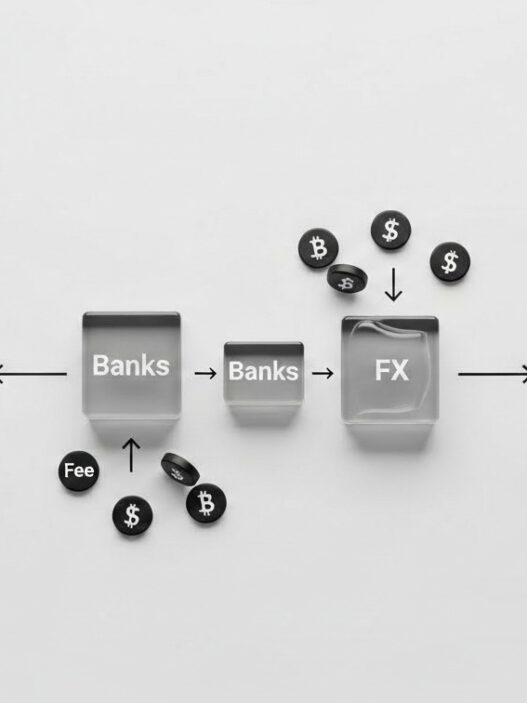
In 2025, privacy is currency. Billionaires, investors, crypto founders, and C-suite executives are no longer asking, “Where can I go?” but instead, “How can I go without anyone knowing I was there?”
According to Knight Frank’s Wealth Report , 47% of UHNWIs now prioritize “invisible luxury” over high-profile visibility. That means no tagged locations. No branded concierge. No digital trace.
The Rise of “Ghost Travel”
The term “ghost travel” has entered elite circles. Coined by a luxury travel advisor quoted in Forbes , ghost travel refers to a set of advanced protocols designed to keep your movements completely off-grid—no manifests, no paper trail, no social breadcrumbing.
It includes:
- Alias-based bookings (via legal entities)
- Private airport terminals with single-client occupancy
- Concierge NDAs
These aren’t paranoid fantasies—they’re the new norm for clients with influence, assets, and enemies.
Alias Bookings & Ghost Addresses — The Billionaire Blueprint
The world’s wealthiest don’t just travel—they vanish.
Alias bookings and ghost addresses have become a staple of elite itinerary planning in 2025. These aren’t tactics born from celebrity paranoia—they’re risk management tools used by private families, crypto founders, high-stakes investors, and politically exposed persons (PEPs). In a digital-first world, the art of disappearing well has become an industry standard.
Booking Under Legal Entities or Shell Corps
Instead of flying under a name, ultra-wealthy travelers now fly under a brand, fund, or offshore trust.
Example: A tech CEO traveling to the Maldives won’t appear on a villa registry. Instead, the rental is booked under an LLC registered to a private family office. The payment is routed through a multi-sig crypto wallet owned by the legal entity—not the individual.
Why it works:
- Avoids direct association with the booking
- Adds layers between identity and transaction
- Reduces personal exposure to surveillance or hacking risks
This is the same strategy used by high-level executives traveling to investment zones or politically volatile regions.
What Are Ghost Addresses?
A “ghost address” is a strategic location used for correspondence, customs, or documentation without revealing the client’s actual residence or point of origin.
Services like Sovereign Man and Nomad Capitalist offer digital and physical ghost address setup for HNWIs and digital nomads who need to separate legal presence from physical presence.
When paired with private jet travel, a ghost address:
- Prevents flight path tracking
- Obscures customs or travel entry data
- Disguises travel intent (e.g., business vs. leisure)
Real-World Use Case
A crypto VC firm flying three partners to a deal closing in Zurich books flights under a Liechtenstein holding company. The aircraft is scheduled out of a private airfield in northern Italy, and lodging is booked using NFTs connected to a DAO wallet. No names, no trail, no press leaks.
Tools of Disappearance — Crypto, VPNs & Surveillance Shields
In 2025, traveling anonymously isn’t just a preference for HNWIs—it’s a strategy. To execute ghost-mode travel effectively, elite flyers deploy an arsenal of tools designed to block surveillance, mask transactions, and protect digital trails from even the most sophisticated eyes.
Encrypted Wallets & Multi-Sig Transactions
Privacy-first travelers no longer rely on a single Bitcoin wallet. Instead, they use multi-signature wallets like Casa (nofollow) or Gnosis Safe (nofollow), often managed through a family office or concierge.
These wallets:
- Require multiple confirmations before a transaction completes
- Make it nearly impossible to trace ownership to an individual
- Offer real-time revocation in case of device compromise
Example: A villa in the Seychelles is booked using ETH from a DAO-governed wallet. The wallet’s multi-sig system requires sign-off from both the traveler and their CFO or advisor.
Enterprise-Grade VPNs & Burner Devices
VPNs like Proton VPN or Mullvad aren’t optional anymore—they’re baseline.
But advanced users go a step further:
- Burner laptops bought in cash, used only on secure travel Wi-Fi
- Encrypted phones like Silent Circle’s Blackphone
- No digital assistants (Alexa, Siri, Google) enabled while abroad
This reduces:
- IP leakage
- Device fingerprinting
- Microphone/sensor eavesdropping
Anti-Tracking Tools in Private Aviation
Private jets now come equipped with optional transponder masking services, available through select charter firms like PrivateCharterX . These services can anonymize tail numbers and adjust flight plans in real-time to avoid public radar detection tools like FlightAware or ADS-B Exchange.
Flight privacy has become a luxury differentiator in itself.
Zero-Knowledge Identity Tools
Web3-based identity platforms like BrightID or Polygon ID allow you to verify access to NFT travel memberships without revealing your identity.
Use case: Enter a members-only resort by scanning a token on-chain rather than providing a passport scan at check-in.
The Rise of Alias Travel Advisors & Ultra-Discreet Booking Networks
Gone are the days when even the most expensive concierge services could guarantee privacy. In 2025, a new breed of travel fixer has emerged: the alias travel advisor.
Who Are Alias Travel Advisors?
Alias travel advisors specialize in handling ultra-private bookings for billionaires, celebrities, and crypto whales. They operate under NDAs, use pseudonymous identities, and often manage bookings through shell companies or blockchain DAOs.
Many are former intelligence operatives or cybercrime consultants.
Their responsibilities include:
- Securing unlisted villas, jets, and yachts with zero digital trail
- Coordinating multi-currency or on-chain payments
- Vetting resort staff and transport operators for discretion
- Managing shadow itineraries for decoys or media misdirection
Trusted Networks: These advisors don’t work with OTAs (Online Travel Agencies). They tap black-book networks like:
- Knightsbridge Circle
- The Fixer Lifestyle
- Invitation-only arms of Virtuoso
Booking Through Encrypted Channels
Bookings are executed via:
- End-to-end encrypted messaging (Signal, ProtonMail)
- Temporary anonymous wallets on chains like Monero or Secret Network
- Air-gapped devices and in-person QR code transfers
PrivateCharterX offers enterprise-grade onboarding for advisors booking on behalf of clients. Through tokenized profiles and multi-wallet dashboards, agents can manage multiple identities under a single, secured interface.
→ Explore PrivateCharterX’s Discreet Booking System
Code Language in Reservations
In some cases, reservations are made using code language or through decoy bookings (e.g., booking an “art retreat” that’s actually a secure villa). Advisors use unique terminology for locations, clients, or staff to obscure intent during calls or emails.
Invisible Itineraries — Decoy Plans, Flight Gaps & Ghost Destinations
For HNWIs and public figures, disappearing discreetly isn’t just luxury—it’s necessity. In 2025, the logistics behind elite privacy travel are nothing short of espionage.
Decoy Itineraries: The Art of Misdirection
Many elite travelers today operate with dual itineraries—a public-facing one (for PR teams or media scrutiny) and a true itinerary known only to a small circle. Alias advisors work with security consultants to construct:
- Red herring hotel bookings in major cities (e.g., London, Paris) while the real stay occurs in a remote Tuscan estate.
- Dummy event appearances managed by social media handlers to throw off paparazzi.
- Flight switch decoys, where clients board one jet and disembark discreetly mid-route to connect to another jet without record.
This tactic is commonly referred to as airshadowing in the private aviation space.
Source: A 2024 report by Global Rescue (nofollow) noted that over 40% of their UHNW clients request decoy planning services for international travel.
Gaps in Flight Logs: The Power of Grey Aviation
While most air travel is publicly logged, there are growing networks of grey aviation—unlisted, private brokered flights that operate outside public tracking systems.
Through military-grade transponder blocking, certain aircraft can avoid appearing on tools like FlightRadar24 or ADS-B exchanges. These flights are typically:
- Registered offshore (e.g., Isle of Man, Aruba)
- Chartered through layered LLC structures
- Staffed by security-cleared crews vetted by agencies like Sentinel Aviation
PrivateCharterX partners with specialized brokers to offer ghost leg tracking suppression and tokenized passenger records.
→ Book a Privacy-Optimized Itinerary via PrivateCharterX
Ghost Destinations: Where the Elite Truly Go
You won’t find these locations in any glossy travel mag:
- Neom’s Private Dome Zones – Invite-only pods in Saudi Arabia’s ultra-futuristic city where guests’ presence is not recorded.
- The Ice Strip (Antarctica) – A billionaire-owned airstrip near Queen Maud Land, used for silent nature retreats.
- Tungsten Estates, Norway – Former NATO listening station turned private eco-sanctuary.
These “ghost destinations” are reserved for elite circles, often requiring biometric pre-clearance and crypto deposits held in NFT contracts.
Biometrics & Blockchain — The New VIP Passports
In the world of ultra-private, luxury travel, the traditional passport is becoming obsolete. In its place, biometric identity tokens and blockchain-based clearance systems are emerging as the gold standard for seamless, secure, and exclusive mobility.
NFT-Backed Identity: The Rise of Digital Passports
In 2025, forward-looking HNWIs are storing their travel credentials on-chain.
Projects like Travlr.ID (nofollow) allow clients to tokenize key identification documents—including KYC/AML clearance, vaccination status, and preferred visa zones—into NFT identity wallets. These are:
- Encrypted via biometric signatures (retina, palm, voice)
- Accessed via luxury concierge blockchain apps
- Used to bypass traditional customs at crypto-friendly terminals
Case Study: An entrepreneur traveling from Dubai to Zurich via PrivateCharterX used an NFT-backed “GreenList” pass to clear customs in under 3 minutes. The flight was fully booked using ETH and the clearance was tied to a retina-scan wallet synced with AuthChain.io.
Biometric Boarding & AI Verification
High-end terminals in cities like Geneva, Singapore, and Abu Dhabi now use face-scanning, gait analysis, and voiceprint access for ultra-fast, zero-interaction boarding.
These systems are especially critical for:
- Celebrity clients needing zero-contact visibility
- Politicians or royalty flying under code-name manifests
- Entrepreneurs traveling with high-stakes, high-security data
PrivateCharterX collaborates with biometric vendors to offer zero-document travel for qualified clients on select routes.
Blockchain Visa Systems
Some governments are now piloting Web3-based visa protocols that allow visitors to:
- Store visas on-chain
- Renew access automatically via DAO approval
- Link entry rights to wallet activity or NFT-based membership tiers
For example, the Estonian e-Residency DAO is currently testing a blockchain visa that allows Web3 entrepreneurs and investors to enter the country using a digital identity wallet.
Pricing Privacy — What It Costs to Disappear (and Why Some Pay It Willingly)
For the ultra-wealthy, true freedom isn’t about visibility—it’s about invisibility. In the age of surveillance, anonymity has become the new luxury, and the price tag reflects it.

The Cost of Going Dark
Creating a “disappeared” digital and physical identity—without compromising luxury—can cost $250,000 to over $5 million annually depending on scope. Here’s where that money goes:
| Privacy Asset | Typical Annual Cost | Purpose |
|---|---|---|
| Alias-Based Travel Concierge | $80,000+ | Manages crypto payments, booking aliases, and burner logistics |
| Biometric-Protected Real Estate | $1M–$3M | Hidden estates with facial-gated access & no digital footprint |
| Private Jet Routes via Non-Commercial Terminals | $300,000+ | Reduces visibility, bypasses major security & customs |
| On-Call Ex-Intelligence Security | $250,000+ | Personal protection without public-facing trails |
| Legal Privacy Trusts | $150,000+ | Manages off-shore ownership of yachts, jets, and crypto properties |
Source: Knight Frank Wealth Report 2025 , Sovereign Wealth Intelligence Group
High-Net-Worth Privacy Habits in 2025
A recent survey of 238 UHNWIs (via Campden Wealth) found:
- 71% have a “second name” travel profile
- 43% use burner wallets for travel-related crypto transactions
- 28% work with advisors to digitally erase travel metadata within 24 hours of arrival
Internal Link Opportunity: Read more on anonymous crypto villa rentals

Privacy vs. Paranoia: The Justification
Entrepreneurs in tech, Web3, and AI are uniquely targeted by:
- Deepfake impersonation schemes
- Competitor espionage
- Targeted cyber-extortion
Privacy isn’t just about discretion—it’s about operational security, reputation management, and digital risk mitigation.
As one founder of a VC-backed AI firm stated:
“My net worth isn’t what makes me a target. My ideas are.”
This is why PrivateCharterX offers on-demand vanishing protocols — including masked manifest bookings, satellite relay travel routes, and token-gated concierge coordination.
How to Build Your Own High-Profile Privacy Stack (Without Breaking the Law)
Privacy at this level isn’t just about secrecy — it’s about strategy, systems, and staying ahead of the curve. Here’s how elite travelers structure their privacy-first lifestyle without skirting legal lines.
Step 1: Build an Alias Travel Identity
- Create a travel shell using a legal alias or LLC-operated trust.
- Use crypto wallets registered to corporate entities for travel payments.
- Use email masking tools (like ProtonMail aliases) for all booking-related correspondence.
Recommended Tools:
- ProtonMail Secure Email
- Privacy.com – Burner payment cards
- BitPay for Businesses – Enterprise crypto payments
Step 2: Use a Privacy-Centric Travel Advisor
Forget booking through public platforms. HNWIs work exclusively with advisors trained in:
- Alias booking and identity masking
- Burner device coordination
- Non-disclosure protected concierge networks
Want this handled? → Work with a crypto-secure advisor at PrivateCharterX
Step 3: Mask Your Itinerary in the Metadata
Yes, your iPhone and Gmail know exactly where you are.
Best practice: Use secure routers, encrypted devices, and “silent” airspace routes when traveling.
Luxury tools for metadata masking:
- Silent Link – Private eSIMs that leave no roaming trail
- Purism Laptops – Privacy-first hardware for founders on the move (nofollow)
Step 4: Store & Share Your Data in Tokenized Vaults
Create a token-gated data vault for your documents, flight history, and identity profiles. Think of it like a cold wallet for your travel DNA.
Why Flight Record NFTs Are Changing Aviation Ownership
Vault providers to explore:
- Sovereign Keys – Web3 identity vaults
- Obsidian Vaults – Private decentralized file storage
Step 5: Rotate Routes, Devices & Digital Signatures Quarterly
This is what private intelligence firms call “operational hygiene.” The elite don’t just mask identity — they rotate it.
Example protocol:
Never use public booking apps (Skyscanner, Google Flights, etc.)
Rotate phones every 90 days
Use ephemeral wallets (e.g. MetaMask Burner)
Design Your Personalized Privacy Protocol
Ready to vanish — luxuriously?